Tag: vultr
-

TurboVPN
TurboVPN is a virtual private network (VPN) service that allows users to browse the internet securely and anonymously. However, before investing in this service, it’s important to consider the ownership of TurboVPN. TurboVPN is owned and operated by Innovative Connecting Pte. Limited, a Singapore-based company. While the company has been in business since 2016 and…
-

McAfee VPN
It’s highly likely that you’re familiar with McAfee if you’re acquainted with any company in the realm of digital security and virus protection. Founded in the United States in 1987, McAfee has gained notoriety primarily for its antivirus software. However, upon discovering that they also offer a VPN service, we felt compelled to put it…
-

Aloha Browser VPN
The Aloha Browser is one of the up-and-coming new browser apps for mobiles which targets one of the most important aspects of modern browsing — privacy. The Aloha Browser is the only browser (to our knowledge) that comes with a built-in VPN and encrypts user data at all levels. When you are using Aloha VPN…
-

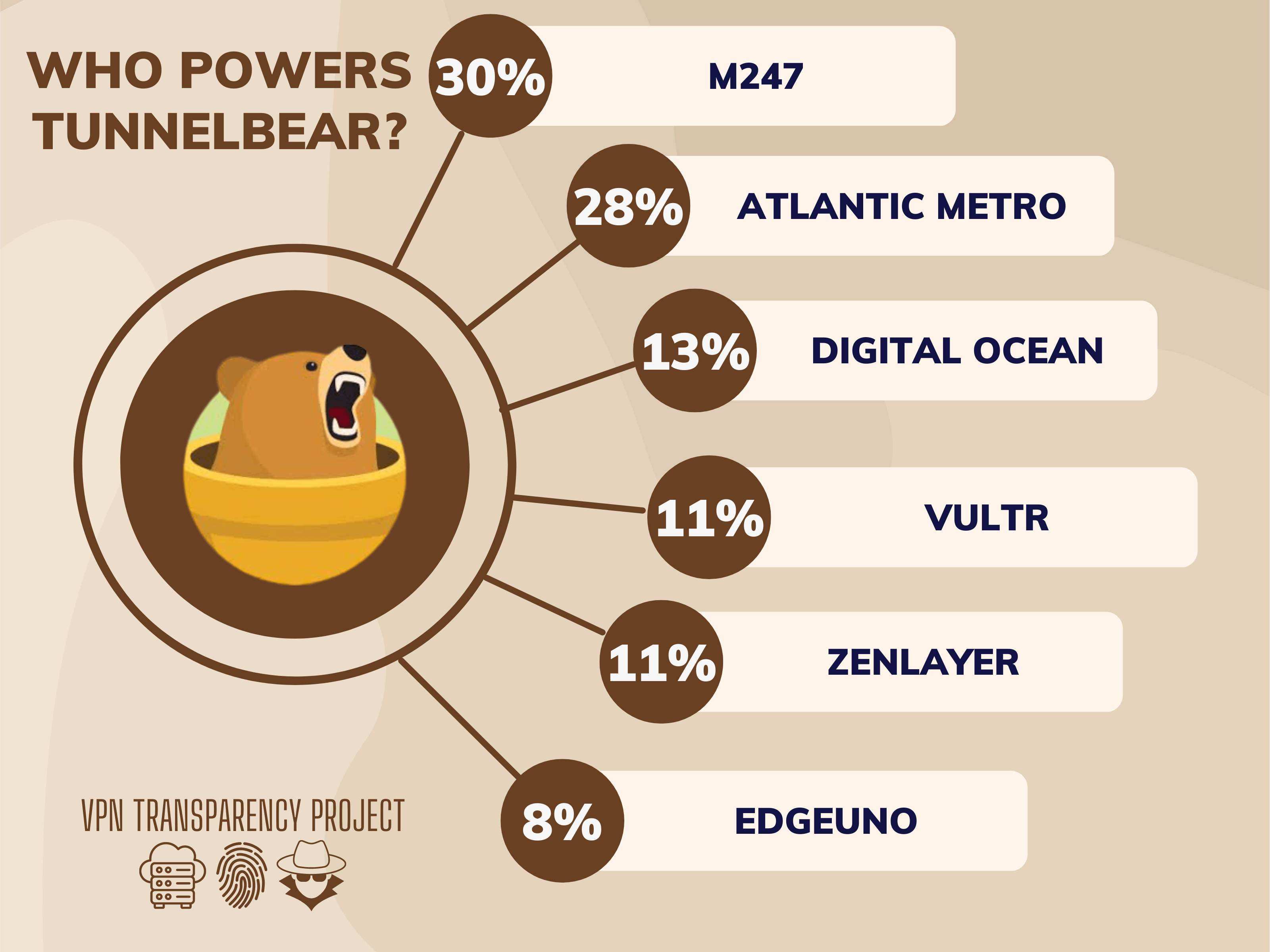
TunnelBear
TunnelBear is a virtual private network (VPN) service that is known for its user-friendly interface and its commitment to privacy and security. The company was founded in 2011 and is headquartered in Toronto, Canada. TunnelBear offers a range of VPN services that are designed to protect users’ online privacy and security by encrypting their internet…