Tag: estnoc
-

X-VPN
X-VPN is a freemium VPN service that has become well-known for its simplicity and extensive server network. However, these points are overshadowed by some major concerns, making it a questionable choice for privacy-conscious users. One key issue is the existence of adware built into its app, making it a risky choice for users valuing privacy…
-

McAfee VPN
It’s highly likely that you’re familiar with McAfee if you’re acquainted with any company in the realm of digital security and virus protection. Founded in the United States in 1987, McAfee has gained notoriety primarily for its antivirus software. However, upon discovering that they also offer a VPN service, we felt compelled to put it…
-

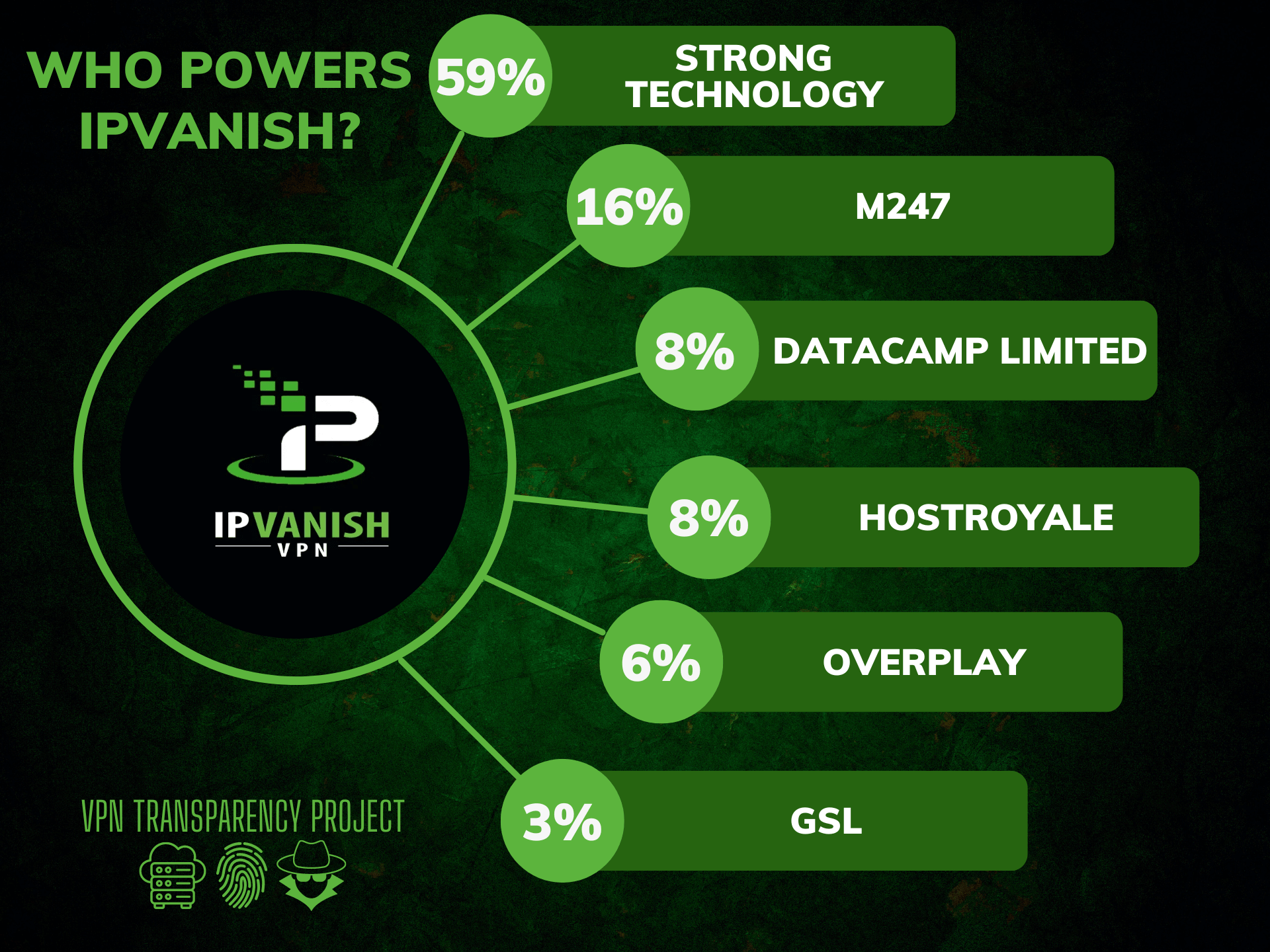
IPVanish
IPVanish is a virtual private network (VPN) service that allows users to securely and anonymously access the internet. A VPN creates a secure, encrypted connection between a device and the internet, protecting data and preventing snooping or tampering by third parties. IPVanish offers a range of VPN products and services, including support for Windows, Mac,…
-

Windscribe
Windscribe, a cross-platform virtual private network (VPN) service provider, was founded by Yegor Sak and Alex Paguis in 2016. Based in Canada, it has grown to operate internationally, supporting a broad range of operating systems and platforms, and providing services to personal computers, smartphones, routers, and smart TVs1. The company’s offerings include OpenVPN, Internet Key…
-

Surfshark
Surfshark VPN is one of the most popular VPN services in 2022. Its competitive price and unlimited simultaneous connections make it a very attractive VPN option for all kinds of users. But does this VPN live up to give the actual value for money that it claims? Surfshark also offers thousands of servers worldwide, excellent…
-

ExpressVPN
ExpressVPN was launched in 2009 by serial entrepreneurs Peter Burchhardt and Dan Pomerantz. From its inception, ExpressVPN’s commitment to privacy and security would be called in to question as several unsettling events unfolded. The service would eventually be acquired by Kape Industries (see more below) for just shy of 1 billion dollars. You have to…
-

ProtonVPN
ProtonVPN is a virtual private network (VPN) service provided by Proton Technologies AG, the company behind the email service ProtonMail. ProtonVPN was created to provide a secure, private, and censorship-free internet connection to people all over the world. It encrypts your internet connection and hides your IP address, making it difficult for hackers, ISPs, and…
-

CyberGhost VPN
CyberGhost VPN was founded in 2011 in Bucharest, Romania, and initially began as a free VPN service. By the following year, it had gathered around 1.7 million users. In 2017, a notable change occurred when Kape Technologies (then known as Crossrider) acquired CyberGhost VPN. This acquisition brought about concerns among observers due to Crossrider’s background…
-

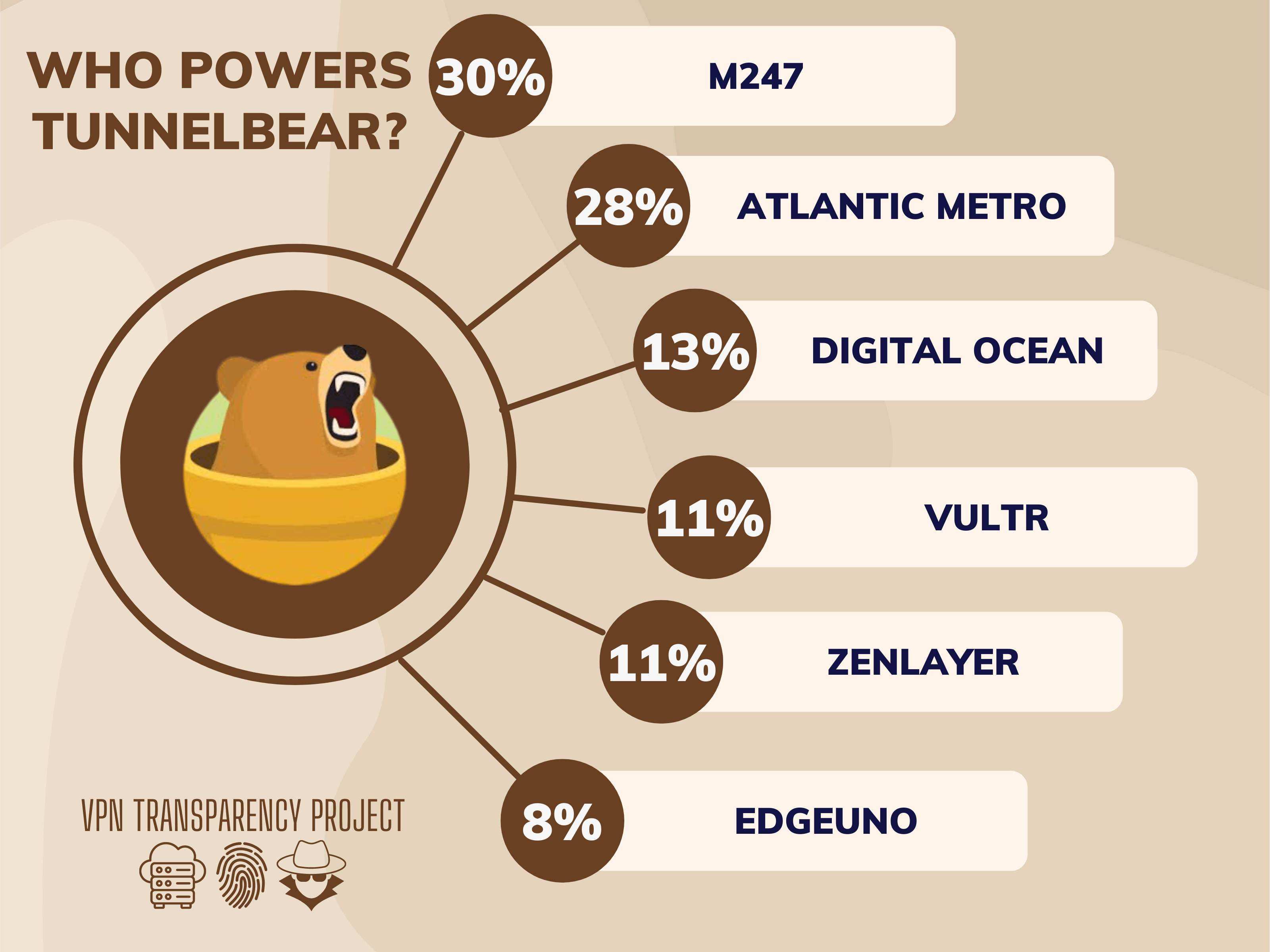
TunnelBear
TunnelBear is a virtual private network (VPN) service that is known for its user-friendly interface and its commitment to privacy and security. The company was founded in 2011 and is headquartered in Toronto, Canada. TunnelBear offers a range of VPN services that are designed to protect users’ online privacy and security by encrypting their internet…
-

TorGuard
Table of Contents Network Overview 2019 Security Incident Global Coverage Related Posts TorGuard is a virtual private network (VPN) service that encrypts internet traffic and helps to secure online activity. It is designed to protect privacy and increase security, and is often used to bypass internet censorship and access blocked content. TorGuard is based in…